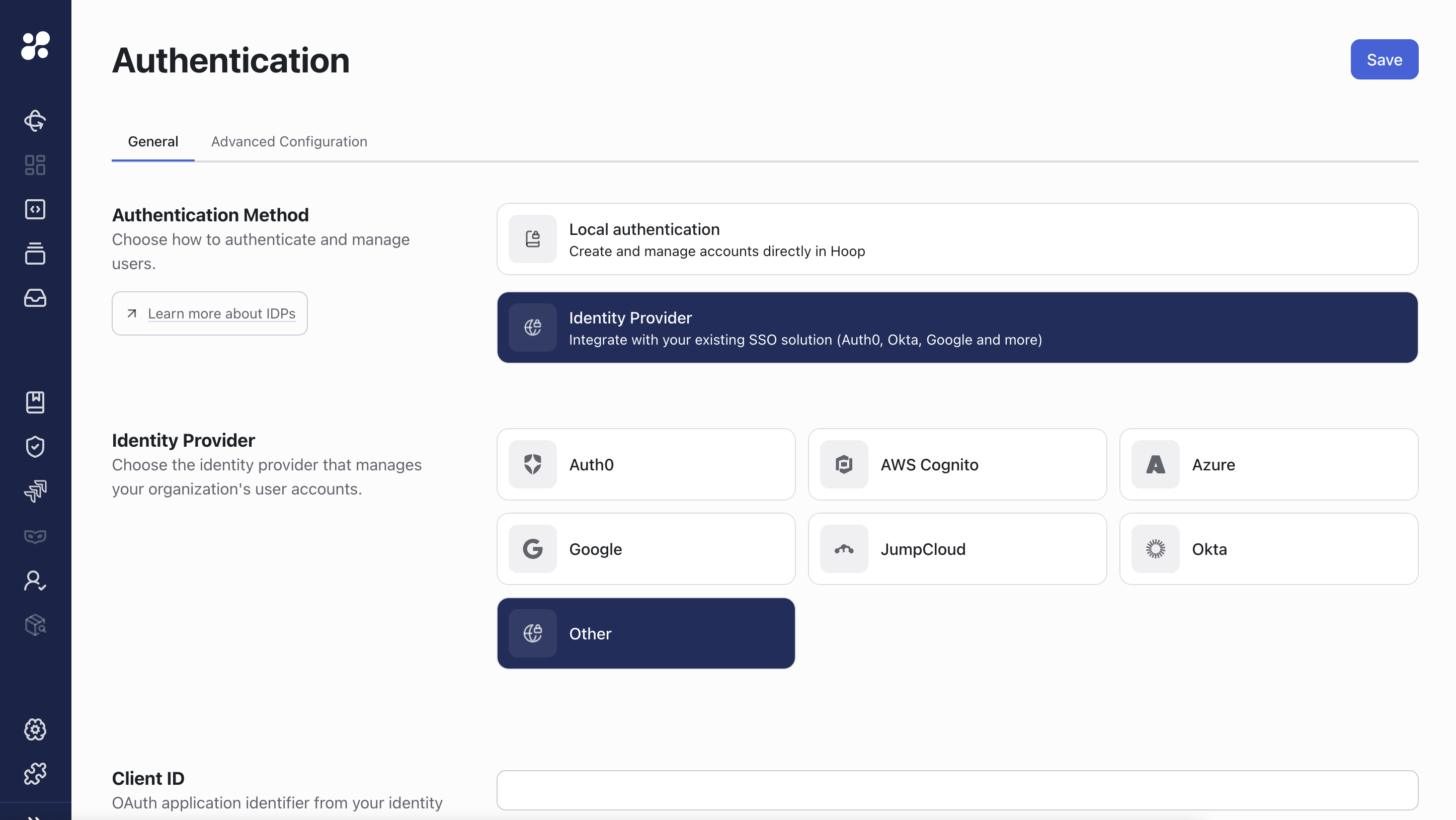
We support a variety of Identity Providers to authenticate users in hoop.dev. In this guide you will find the IDPs we had success integrating with but as due to how we integrate with them using OIDC standards, you can try to integrate with any OIDC compliant IDP.
Users
Users are active and assigned to the default organization when they signup. A user could be set to an inactive state preventing it from accessing the platform, however it’s recommended to manage the state of users in the identity provider.
- The
sub claim is used as the main identifier of the user in the platform.
- The profile of the user is derived from the id_token claims
email and name.
When a user authenticates for the first time, it performs an automatic signup that persist the profile claims along with it’s unique identifier.
Groups
Groups allows defining who may access or interact with certain resources.
- For connection resources it’s possible to define which groups has access to a specific connection, this is enforced when the Access Control feature is enabled.
- For access requests, it’s possible to define which groups are allowed to approve an execution, this is enforced when the Access Requests feature is enabled.
This resource could be managed manually via Webapp or propagated by the identity provider via ID Token. In this mode, groups are sync when a user performs a login.
Roles
- The admin group is a special role that grants full access to all resources
This role should be granted to users that are responsible for managing the Gateway. All other users are regular, meaning that they can access their own resources and interacting with connections.
- The auditor group grants the auditor role that gives read only access to session resources
Configuration Page
This feature is available beginning with version 1.38.12
After the configuration is saved, the identity provider will be automatically reloaded with the new settings.
The environment variables will not be considered as part of the configuration.
Troubleshooting
The IDP configuration experience could lock yourself out of the application if not configured correctly.
To wipe all the configuration, connect in the Hoop Postgres database and the delete the following row:
-- clear all configuration
DELETE FROM private.authconfig WHERE org_id = (SELECT id FROM private.orgs);
UPDATE private.authconfig
SET admin_role_name = 'my-new-admin-role-group'
WHERE org_id = (SELECT id FROM private.orgs);
In the upcoming releases we will improve this experience to avoid this situation.