AWS RDS IAM Authentication
You can authenticate to your DB cluster using AWS Identity and Access Management (IAM) database authentication. IAM database authentication works with PostgreSQL, MySQL. With this authentication method, you don’t need to use a password when you connect to a DB. Instead, you use an authentication token.Feature Overview
| Database | Native | One off | Description |
|---|---|---|---|
| PostgreSQL | ✔️ | ✔️ | Supports IAM authentication for PostgreSQL RDS instances using Native connections and Webapp |
| MySQL | ✔️ | ✔️ | Supports IAM authentication for MySQL RDS instances using Webapp only |
Configuration
Configure AWS RDS IAM Authentication in your AWS
- Follow the steps in the AWS Documentation to enable IAM authentication for your RDS instance.
- Make sure your AWS has the policy for IAM database access For example, the policy below allows the user db-user to connect to the database cluster-ABCDEFGHIJKL01234 using IAM authentication.
arn:aws:rds-db:us-east-2:111122223333:dbuser:cluster-ABCDEFGHIJKL01234/db_user2rds_iam to the user to be able to connect using IAM authentication.
You also need to grant permissions if the db_user needs to read and write to databases and schemas.
For example, GRANT SELECT ON ALL TABLES IN SCHEMA public TO db_user; - this will be the permission you will have when connecting via Hoop.Configure the Role on your agent
Make sure your agent has the AWS credentials configured or can assume an AWS role that can use the policy created previously to be able to generate the auth token.
If you deploy your agent on Kubernetes, you need to assume the role. For example: The code example may need to be adjusted to fit your specific setup.
HoopRdsIamRole is the role that has the policy to create tokens for connecting to RDS using IAM authentication.If the agent runs in Kubernetes on EKS, then the best practice is to use IRSA (IAM Roles for Service Accounts). The trust policy for the EKS cluster OIDC provider is shown below. The code example may need to be adjusted to fit your specific setup.
If the agent runs on an EC2 instance, you can attach the role to the instance profile.
Alternatively, you can add the AWS credentials as environment variables in your agent:
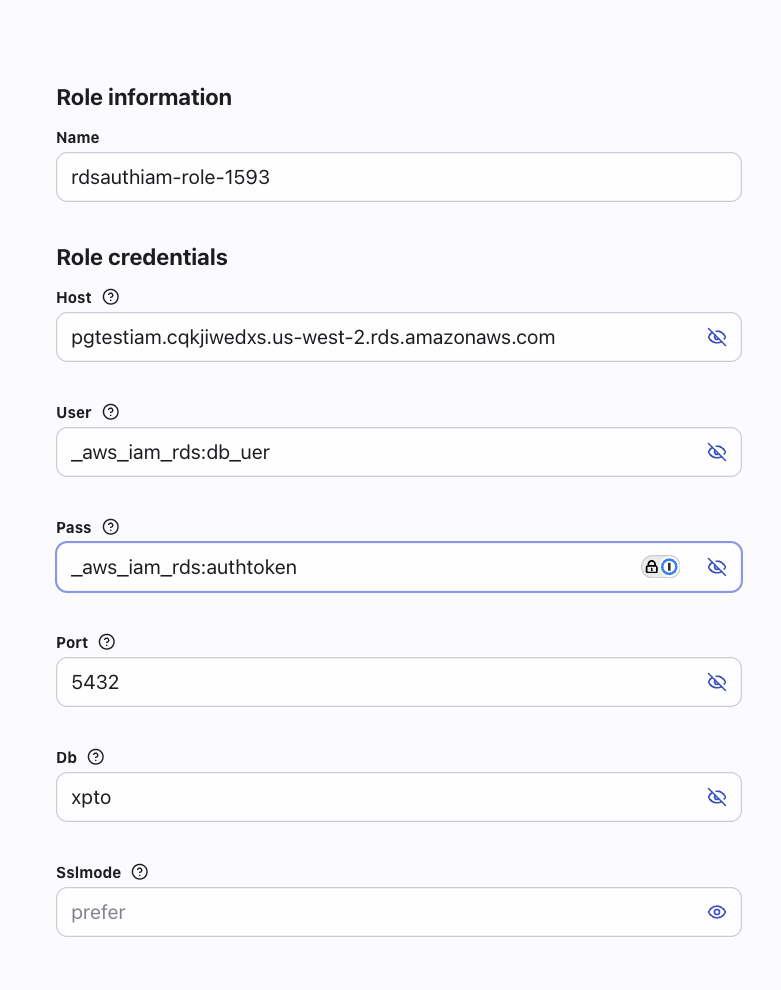
Configure the AWS Auth on Hoop
When creating a new role, the User and Pass information must follow the following format:
- User:
_aws_iam_rds:db_user - Pass:
_aws_iam_rds:authtoken