Requirements
- An account in OKTA
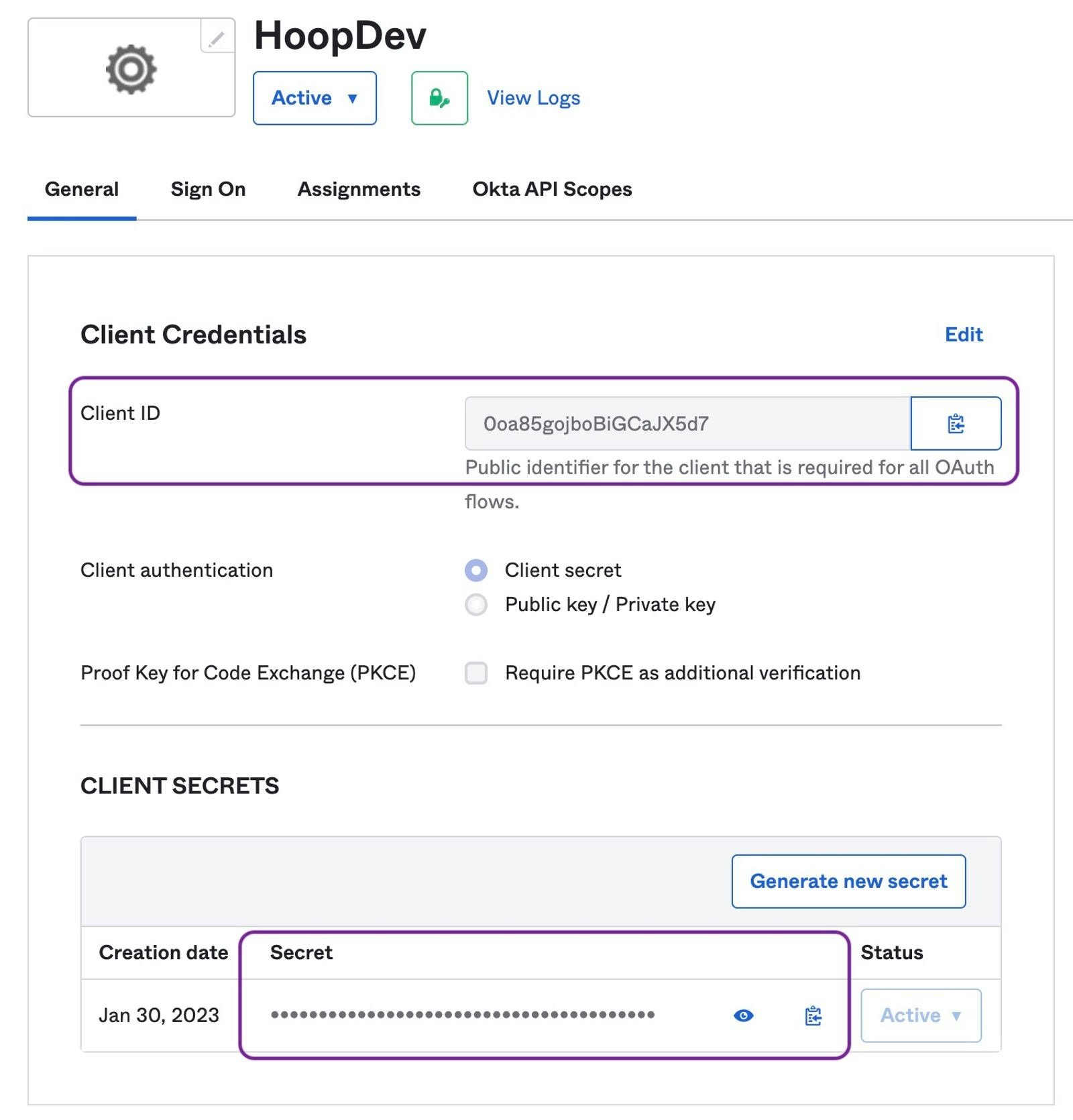
API_URLis the public DNS name of the hoop gateway instance
API_URL address.
Identity Provider Configuration
Create an Application
- Go to
Applications > Applicationsand click on the Create App Integration button - In Sign-in Method, select OIDC - OpenID Connect
- In Application type, select Web Application
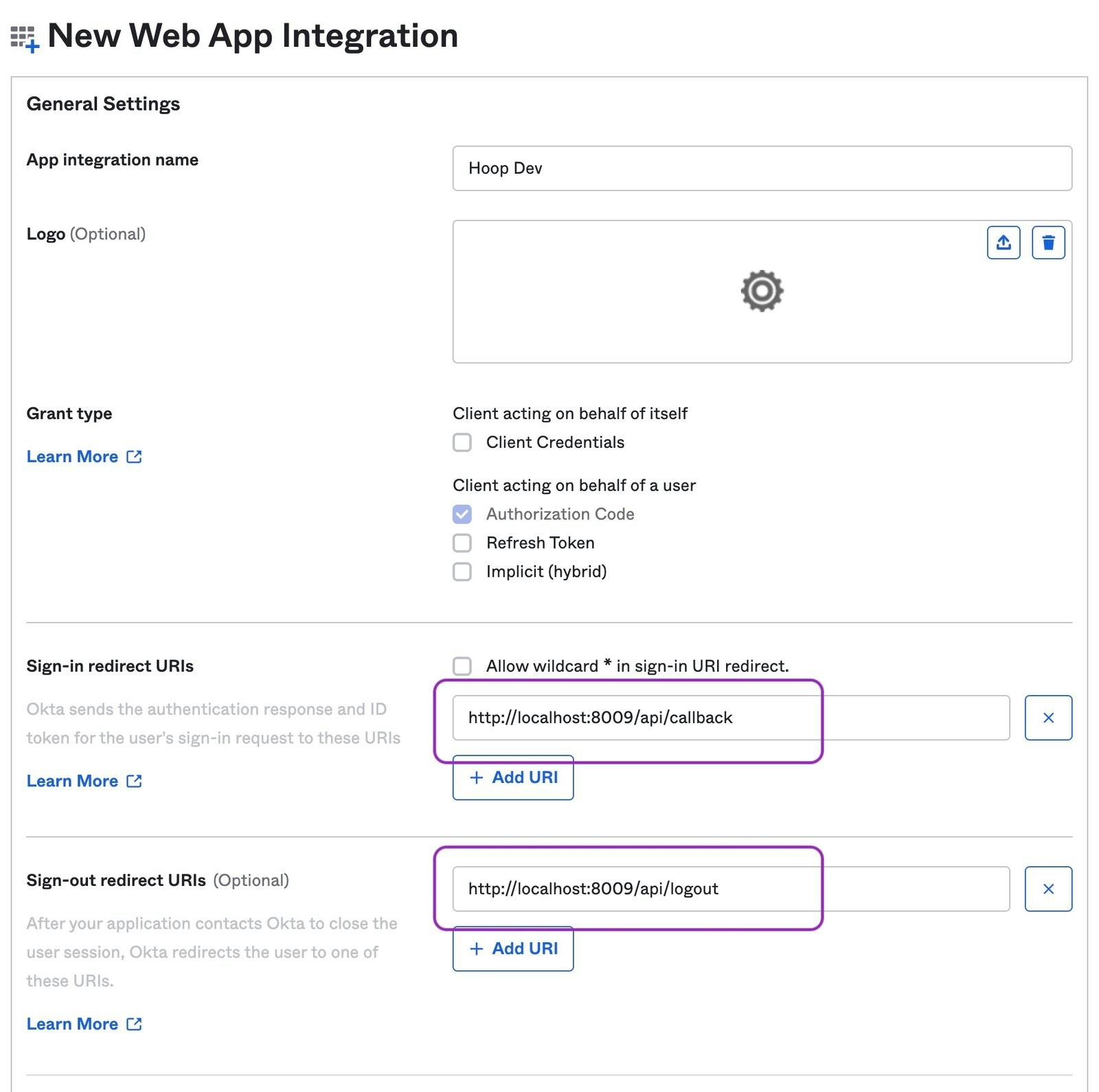
Configure the Redirect URIs
- Signin redirect URIs:
{API_URL}/api/callback - Signout redirect URIs:
{API_URL}/api/logout
Collect Issuer Information
- The Issuer URI depends on the authorization server being used. Refer to this documentation.
If Okta does not allow external applications to validate access tokens, add the query string option
_userinfo=1 when configuring the Gateway. It indicates to use the user info endpoint.
The _userinfo value is removed when used to exchange information with the identity provider.Configuring Groups
Explains how to configure groups claim to propagate when users sign in.Refer to Okta’s Documentation for more information.
Add Groups Claims
- Go to
Security > API > {authorization server} > Claims - Click on
Add Claimsbutton
groups claim for the ID Token to any scope (image below)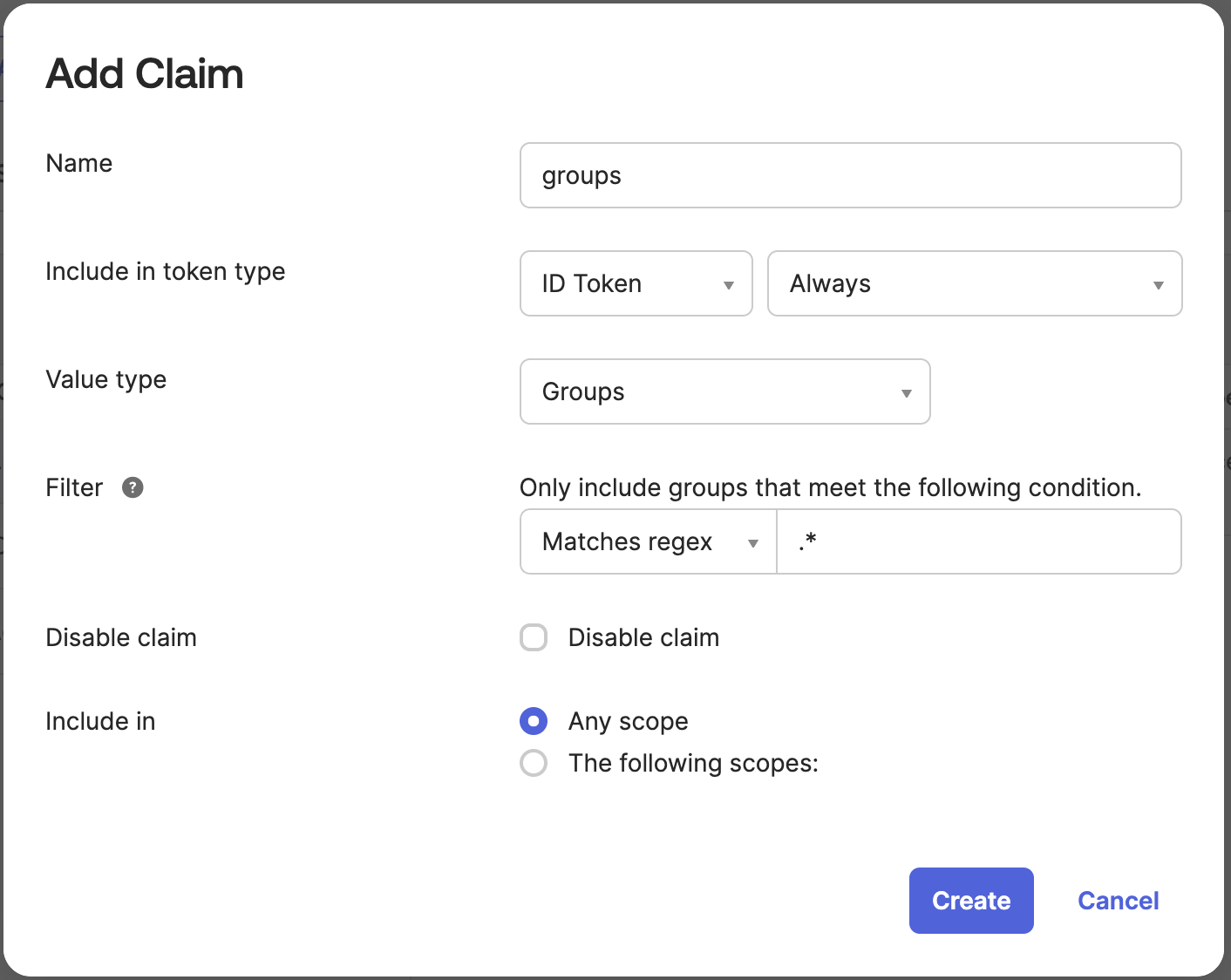
Token Preview Test
This step validate if the configuration is returning the 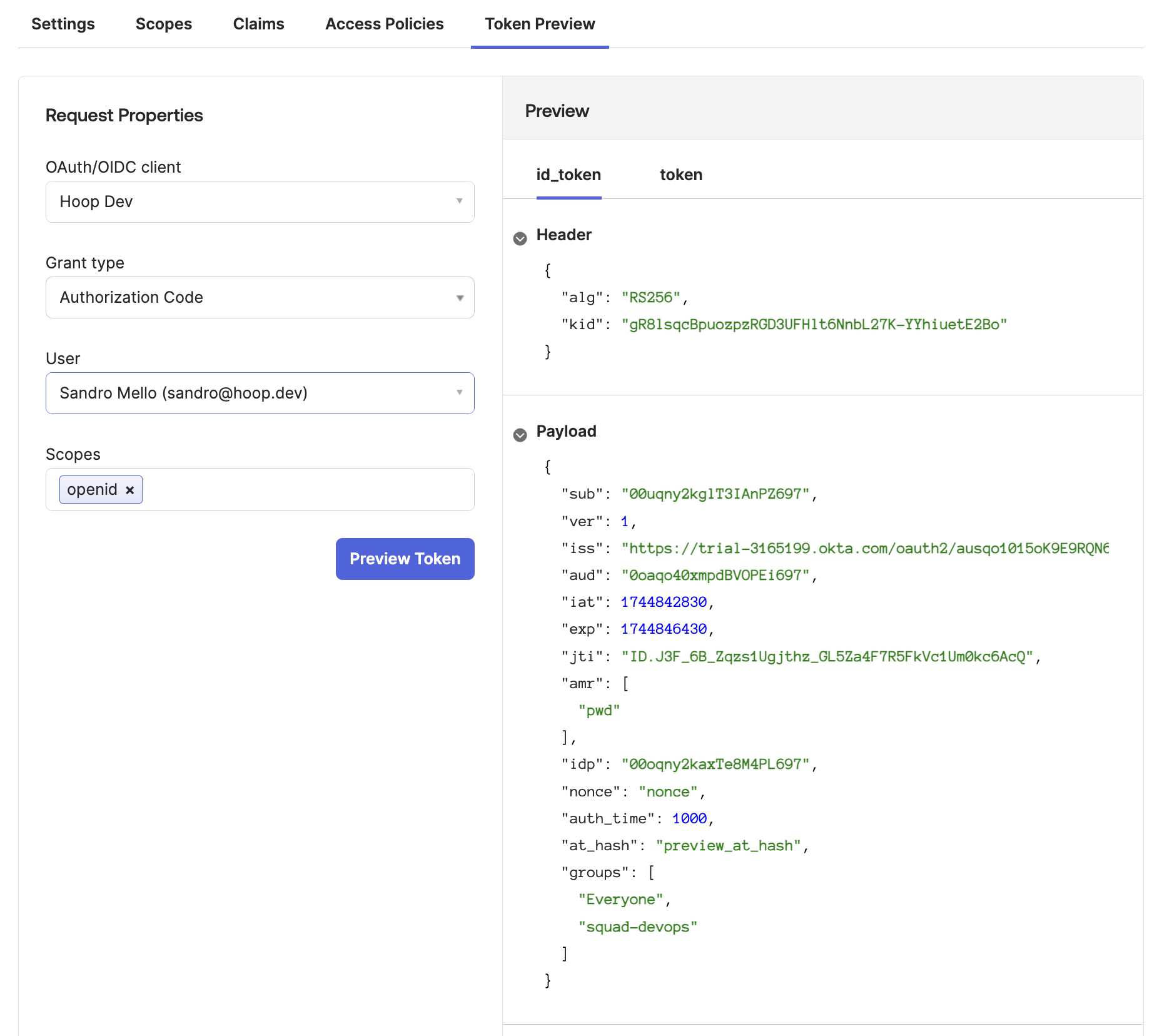
groups claim properly- Go to
Token Previewtab - Select the Hoop Application
- Select the Grant Type as
Authorization Code - Select a user associated with this application
- Add the scope
openid
groups containing the groups associated with your application (image below)
Configure Hoop Gateway
The Hoop gateway requires proper configuration to correctly map claim names for synchronization.
For detailed instructions, please consult the OAuth2/OIDC Authentication Documentation