- Resource Type Selection
- Agent Configuration
- Resource Role Credentials
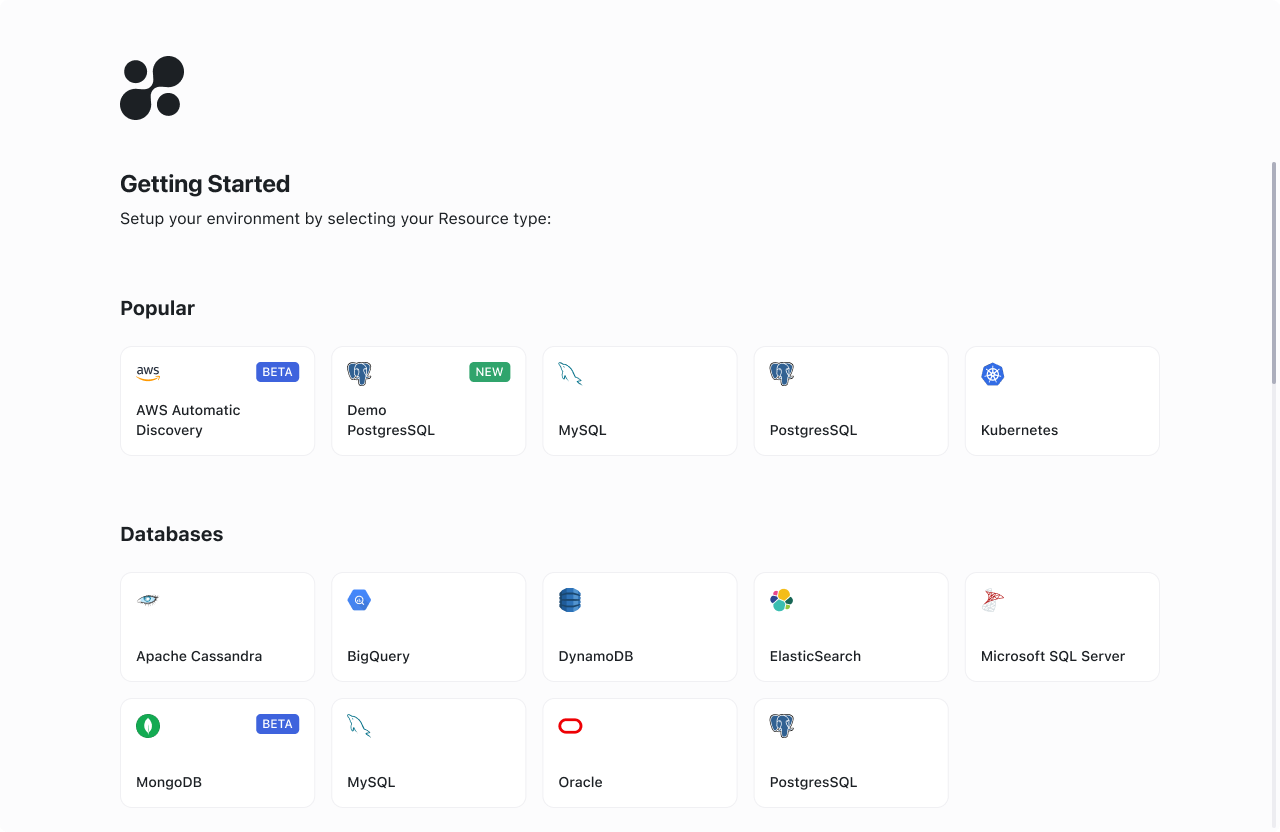
Resource Type Selection
When setting up a new resource, you’ll first choose one of the multiple types of resources available. If you’re not sure what type of resource you need, you can choose the Demo Postgres resource to get started.Agent Configuration
After selecting your resource type, you’ll need to configure the agent that will be used to connect to the resource. You can choose to use the default agent or you can create a new agent. The agent is the component that will be used to connect to the resource. It is responsible for:- Authenticating to the resource
- Connecting to the resource
- Transmitting data to and from the resource
You can learn more about agents in the Agents section.
Resource Role Credentials
After selecting your resource type, you’ll need to provide the necessary credentials and connection details. The required fields vary by resource type.Databases
Databases
- Host address (e.g. localhost)
- Port number (e.g. 3306)
- Username
- Password
- Database name
- SSL mode (Optional)
Linux VM, Container or Console
Linux VM, Container or Console
Linux VM or Container
- Access and manage with terminal commands
Secure Shell Protocol (SSH)
- Private Key (paste your file content)
- SSH URI (ssh://[uri])
Console
- Ruby on Rails
- Python
- Node.js
- Clojure
- Operating system (MacOS/Linux)
- Environment variables (Key-Value pairs)
- Configuration files
- Name (e.g. kub_config)
- Content
- Additional command (optional)
Network Service Access (ZTNA)
Network Service Access (ZTNA)
- TCP
- HTTP (Coming Soon)
- Host address (e.g. localhost)
- Port number
- Agent selection
Additional Configuration
After configuring the agent and the resource role credentials, you will be able to configure additional settings for your resource role on the configuration section.- Add optional tags for organization
- Configure additional security features
- Access Requests - Require approval prior to resource role execution
- Live Data Masking - Automatically mask sensitive data in query results
- and more…
Security Best Practices
Meaningful Names
Use descriptive names that indicate the purpose and environment of the configured resource role.
Tag Organization
Utilize tags to categorize and manage resource roles effectively.
Enable Access Requests
Set up access requests for sensitive resources to maintain security.
Data Protection
Enable Live Data Masking when handling sensitive information.