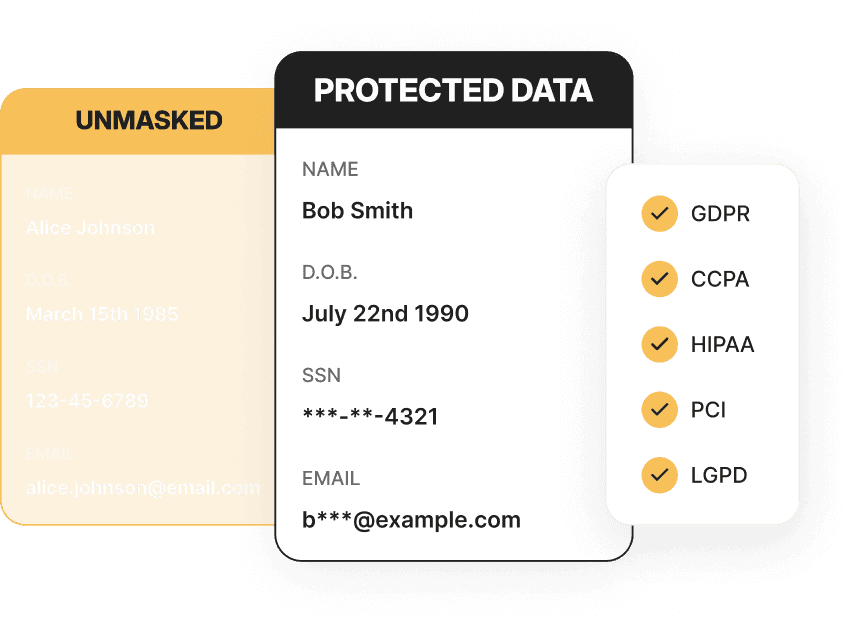
AI Data Masking
Give testers safe access to sanitized production data.
Meet PCI DSS, GDPR, SOC 2, and HIPAA data privacy controls without overhead.
Allow models to train on production like data without risk of exposure.
Choose data types, roles, and permissions.
Enable developers to self-serve JIT access to sanitized production data through their CLI, IDE, Coding assistant, or the Hoop.dev gateway.
Add new resources and team
members in a few clicks.
Self service access to sanitized
production data means fewer change failure rates and faster debugging.
Maintain continuous compliance for
sensitive data without overhead.
Remove the primary source of friction
in the SDLC by automating safe
self-service access.
Experience data protection that cuts overhead and speeds up developers.