Access Control Onion
"Great! Now we can move to audit trails", he said with a smile. "Maybe your team should start building or hiring some engineers", I replied to the sec team lead. "Let's take this matter to the CTO", I continued while leaving the room to grab some water.
The meeting goal was to present the SSO solution requested by the sec team and finally get them off our back. The backlog of platform and developer experience items was paused for months. We had been prioritizing security features for a while since SOC2 re-certification was approaching.
Back in the meeting we setup a meeting with the CTO. I had a week to document the problems of the never-ending security backlog we had to implement. And it was in this process that I found a troubling issue: we were working on the wrong problem.
It is impossible to get table stakes of security features for all layers of today's stack
You are wasting your teams' time if working on individual security features.
There are many invisible layers needing security work. Many times these layers are uncovered ad-hoc. Or worst: when they become problems. When this happen it is impossible to think strategically about the platform roadmap. Adding SSO to a VPN is one piece of a large puzzle. Then you have to add SSO to tools folks use with the VPN. Your database need SSO. Your messaging queue. And SSO is only one of the 4A security features. Realizing the size of this problem will reduce your work and enable you to work on higher impact projects.
The first step is to identify what are these invisible layers. Here is how:
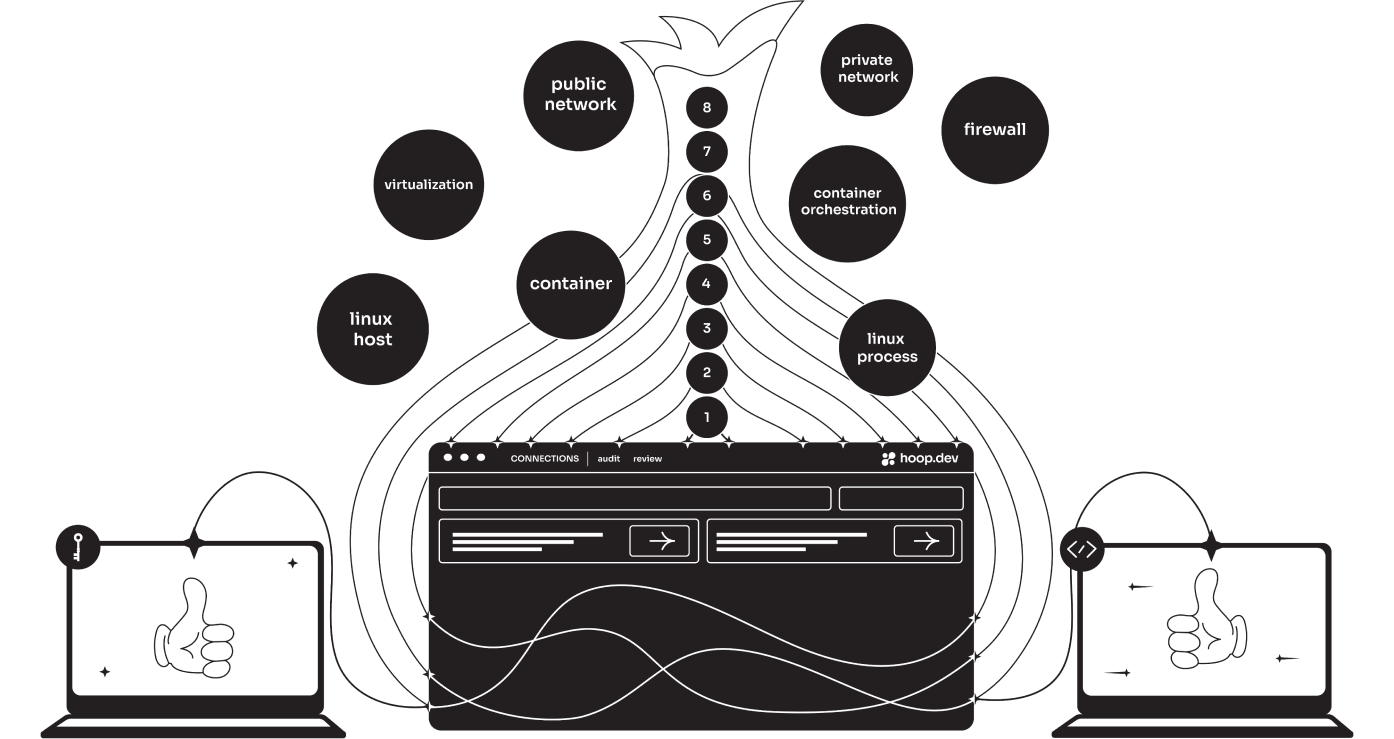
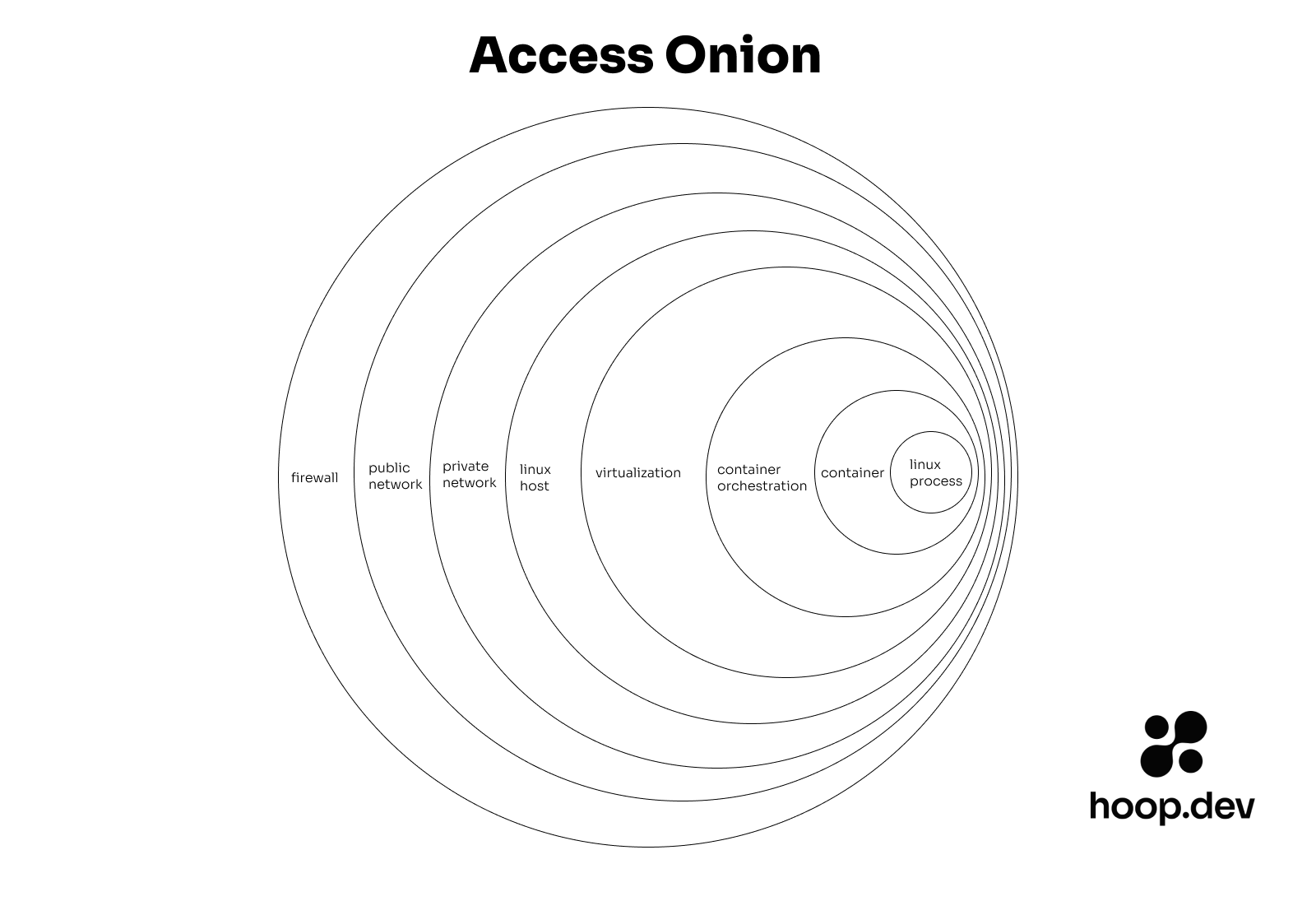
The access onion
Your tech stack keeps growing, and with it the layers of the onion.
Here is what the onion looks like for a tech startup running on AWS with a recent stack. We are only talking about live application process access. Not accounting for access to databases, message queues, cache, etc.
Trying to add the 4As to the onion is impossible
When you multiply the layers of the onion by the four basic security features, it doesn't look good. Do you know the size of your access management backlog?
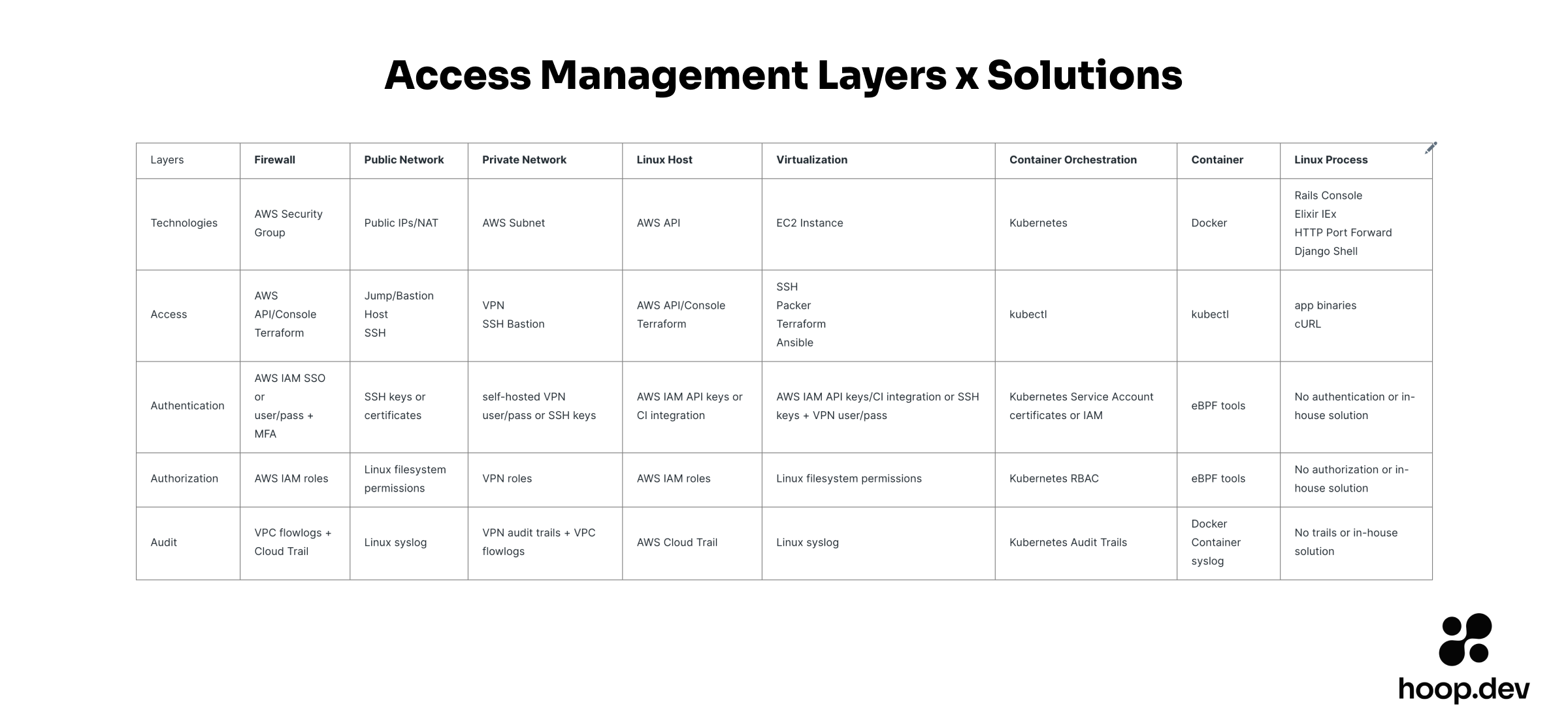
Understand the problem before trying to fix it
"I didn't know we had that many things to do", the CTO said with a worried face starring at the table above. "Yep", I replied, "the platform team can't work on platform features while still in charge of security". The meeting ended with two open roles for engineers that would join the security team.
When you look at one small region of the onion, the problem seems small. Why not just add it to the DevOps team backlog for the week, right? But this ad-hoc type of prioritization prevents teams from moving toward the right goals and it feels like walking in circle. A never-ending security backlog. Try leveraging tools that cover multiple layers of the onion like hoop.dev – and align everyone around the actual size of the problem.
