Zero Trust Network Access
Zero Trust Network, often referred to as Zero Trust Security, is a cybersecurity framework and approach to network security that challenges the traditional security model of "trust but verify." In a Zero Trust model, no one, whether inside or outside the organization's network perimeter, is automatically trusted by default. Instead, trust is continuously verified and never assumed.
But how can we apply this with agile and DevOps teams and methodologies within our organizations?
Zero Trust should be a business enabler, reducing complexity and providing a unified experience for your endpoints.
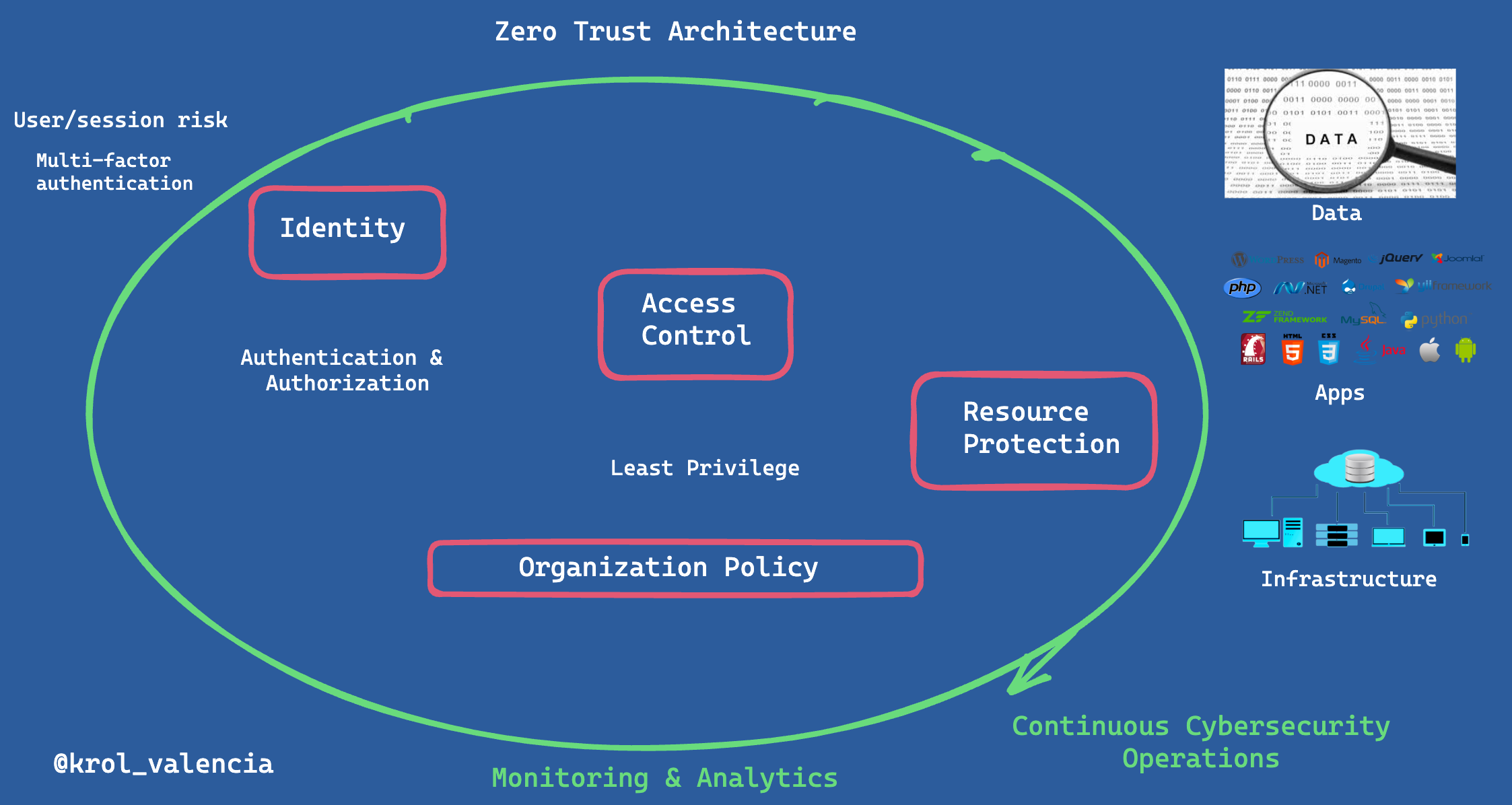
Zero Trust Architecture
Zero Trust Architecture (ZTA) could be very complex, is an enterprise cybersecurity plan that leverages the Zero Trust concept and encapsulates all components of relations, workflow planning, and access policies.
ZTA is designed in response to corporate networks used by remote users, user-owned devices (BYOD), and cloud-based assets that are not within the company's original network boundaries.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is a category of technologies that offers secure remote access to applications and services. Unlike VPNs, ZTNA provides secure access on a per-application basis. To understand ZTNA, it is important to be familiar with its model and frameworks. ZTNA is a component or subgroup of the Zero Trust security model.
By default, traditional network security trusts anyone inside a network once they've been verified. In the zero trust security model, trust is never assumed by default. Instead, users, regardless of location, need to be verified and given only the minimum amount of access they require. This means that a user's request to access application will be verified and authorized only for that specific application.
Access to other applications or resources will not be granted based on previous verification. Instead, each application service is verified independently. Verification methods may vary depending on the implementation, but at a minimum, it includes the following three pillars:
- Identity Context and Security Posture: Identity involves user identification, authentication, and authorization. In other words, it answers the questions of who you are, whether you are who you claim to be, and whether you are authorized for the requested resource. The identification of a user should typically include a second or multi-factor authentication.
- Access control is based on the least privilege security model, which ensures that users are granted only the minimum amount of access necessary for them to access the resource.
- Resource protection: When a user connects, it is important to verify their identity and ensure that they are granted access to the resource. The next question to consider is whether the user's machine is secure. Evaluating the security posture may involve various checks on the user's device to ensure compliance. This can range from ensuring that basic security measures like antivirus software are running, to verifying multiple conditions are met before granting access.
An important thing to know is that zero trust does not stop at just verification once a user has been granted access. Zero trust requires continuous monitoring and validation.
Zero trust network access is a technology that applies the principles of zero trust to secure access to applications and resources. The core technology that enables these principles is known as the "trust broker.”
A trust broker sits between the user and the application, providing logical access boundaries and adhering to the principles of zero trust. This means that the trust broker is responsible for verifying the user's identity, context, and security posture. Once verified, a connection is established between the user and the specific application they are requesting. The trust broker will continuously monitor for changes to the identity context and security posture throughout the session's lifespan.
In practical terms, the trust broker can be a network device or a cloud provider, depending on where the application is located.
The important thing to note here is that the trust broker is usually not a single device, but a decentralized solution consisting of various technologies that make up the control and data plane. The control plane is responsible for managing intelligence and monitoring ZTNA policies, while the data plane handles enforcement and typically establishes the connection between the user and application.
How does ZTNA work?
When a user needs to access a corporate endpoint (database, infrastructure, application, etc.), their identity is authenticated using an Identity Management Solution (IDM) that includes multi-factor authentication. The principles of zero trust ensure that the user is only granted visibility to the applications they are specifically authorized for. When the user attempts to access the resource, their verification context and security posture are verified for that specific application.
If the identity phase is successful, the trust broker establishes a tunnel between the user and the requested application. Once connected, the verification process continuously monitors any changes to the identity context or security posture. If the user needs to access a second application, the entire process is repeated with a new verification process and tunnel establishment for the second application.
When using Zero Trust Network Access (ZTNA), the location of the user is irrelevant. Whether they are physically near the machine or thousands of miles away, the concept of zero trust means trusting no one and verifying everything.
There is no security perimeter anymore, there is no DMZ or VPN.
The intranet may be retained for QoS but not for security.
All network sessions must have authentication and authorization
How Hoop helps
A key component in Zero Trust Network Access (ZTNA) is identity, control policies, and applying minimal privileged access. Check how Hoop can assist you on your journey:
- Identity: Utilizes SSO for resource identification.
- Control Policies: Enforces access control, AI data masking, and minimal authorization on the resources. Users can also create custom policies.
- Minimal Privileged Access: Grants minimal permissions to resources. For example, in a Kubernetes cluster, the "Finance team" is granted access only to the namespace. The goal is to limit resource access and apply minimal privileges whenever possible.
